Game Rules¶
Overview¶
In each lab, you are asked to solve a set of challenges (typically 10 challenges except for the first two weeks). For each challenge, you have to submit three things, namely, a flag, the exploit, and its write-up to the submission site: the flag you captured from the challenge, the exploit that you wrote to get the flag, and the write-up that summarizes how you formulated the exploit (see below).
A flag is a 512-byte hex string (like shown below)
and you can find it in /proc/flag on the CTF server.
$ cat /proc/flag
CB25682B33EF8BF23545A767562A1D5AA33C88EEACC1AE562D950CB9F1E5725D
864725DB51460902ECBD52BA4CBED86A10F3A98A35F6FB71871019702A0E9199
5BC59332C390A3C27D0EC2CE85BC13E956A6027E3171352F90467A8C12346D9A
2A26EE914B3078ED031FDB14BB6224C3D743D79A733FB49EB4E9C1F383CF810E
F6841EE935FE2DA2C57DB4804B6823884B36AE62B08848486918C120E4C2AA94
E1D3F8A6E9E2251AC39E5F37971FB07DFF839E0BC1C4E6C1D4A24E0948F8751B
25BFFE854CD84A8D8E28814398FF192CD9AD37150D83DA872E944DF1552F97DD
1649508E5B9E356925F0762AAF53A4683F48AD4B88C0C863FB03DC5B9C5F77A3
9B3156D4E91ED42B76BDDD3962B39BEAF3520BEC297EC89250F10776A869C2C0
5EAA97231C1F0780B25958FA950816D4DD94C448DF99EC3813183BD20C3006F7
D0825569DAEC45534A355094E4F1A5CC2760F45ED6E8B586DCBA23B27B26E19C
99DDA9B1D17983D1138E3EB7B25BEB927FC34B1FCADEC408CBE7CA04D3E27E39
466D051D4DCA562F292AA623884E9D34BA790E6E46F400F1F6B410F2DDCB8D29
1B0AEBF92CBBA24CB37B8C407F036873C65F568DE58BFD6246ABBABC7D06ADF2
E5A86F2C76E927CF741E8E2B75CAA6530B313EAB80F1C0B7E6B8B22E6D9703C1
A0591DD166168C791A26D32AE6ED3730BA1185B53517436721EE0E3458DB6EF4
Your job is to read this flag by exploiting the distributed challenges.
Taking actions #1 Registration¶
Register your account and receive an api-key
Visit the submission site: You will use the registration menu.
Input your username (preferably your real name), e-mail address (we only accept @gatech.edu account) and click the Email api-key button.
Once you succeed, you will receive an email including your API-key. You will use this api-key when you login to the course website.
Login to your account
Go back to the submission site. You will use the Login menu.
Input your received api-key and click the Submit api-key button.
Now, you can connect to the CTF server and begin your lab challenges. You can find ssh details for a particular lab on Canvas.
# login to one of CTF servers
** Refer to Canvas for ssh information! **
[host] $ ssh lab01@ctf_server_address
# let's start lab01!
[CTF server] $ cat README
[CTF server] $ ./bomb
While solving the challenges on the CTF server, you might need to write your own exploit scripts. Feel free to create a directory inside /tmp to store your files. Note that the CTF server and the accout is shared with all other users, so avoid using directory name that are easily guessable (e.g., /tmp/cs6265), and do not reveal your secret directory name anywhere. Listing files in /tmp is not allowed. Also, we encourage you to take backups of your files (i.e., copying your files from the CTF server to your local machine), since /tmp might get emptied once in a while.
Submit your solution and flag.
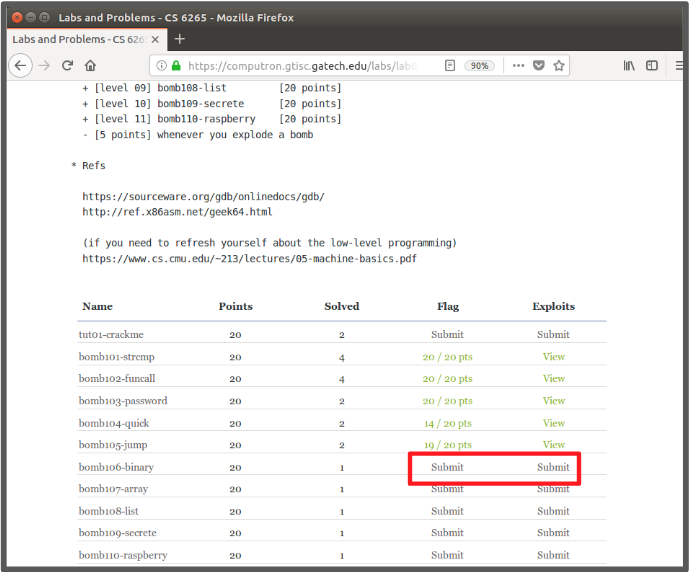
Login → Problems → Submit (Flag / Writeup)
You will get actual score once you submit both flag and write-ups.
Taking actions #2 (Building local environment) - OPTIONAL¶
Although you can solve all challenges on the CTF server, it may be
inconvenient because you may not be able to install your own
toolbox or use restricted tools. In this case, you can build your own
environment. Please not that you still have to read /proc/flag
on the CTF server to get the real flag.
To build your own environment:
Download and install Virtualbox
Download and install the latest version of virtualbox at https://www.virtualbox.org/wiki/Downloads
Windows: Download and install git at http://git-scm.com/download/win
Note: Ubuntu users may want to use the following commands to install Virtualbox
[host] $ sudo apt-get install virtualbox
Download and install Ubuntu 18.04.2 on Virtualbox:
Download the Ubuntu 18.04.2 image.
Launch Virtual box and follow the instructions to install a new VM. A handy walk-through can be found here.
Install essential tools inside VM:
To do labs (lab03 and after):
After launching Virtualbox and Ubuntu VM:
# disable ASLR (before lab05)
[vm] $ echo 0 | sudo tee /proc/sys/kernel/randomize_va_space
# enable ASLR (starting lab05)
[vm] $ echo 2 | sudo tee /proc/sys/kernel/randomize_va_space
# download labXX challenges
[vm] $ scp -r labXX@server:~/[challenge] [your_directory]
# download libc used by the server for analysis (future labs)
# 32-bit
[vm] $ scp labXX@server:/lib/i386-linux-gnu/libc-2.27.so [your_directory]
# 64-bit
[vm] $ scp labXX@server:/lib/x86_64-linux-gnu/libc-2.27.so [your_directory]
# tackle challenges
[vm] $ cd [your_directory_for_challenge]
[vm] $ cat README
...
Feel free to ask for any help on Ed Discussion, or at the office hours if you have any trouble during the setup.
General rule¶
If not specified (e.g., first two weeks), we will follow the scoring rules stated below:
One or two tutorial(s) and 10 challenges every week.
Each challenge is worth 20 points (flag) x 1.0 (write-up & exploit) = 20 points.
If you do not submit the write-up, you get 0 point (20 x 0 = 0).
Maximum points you can get each lab: 220 or 240 points
220 if one tutorial (20 x 11 flags)
240 if two tutorials (20 x 12 flags)
Bonus: first and second bloods (i.e., fastest solvers) will get 2 and 1 bonus points, respectively for each challenge (only for lab03 and after).
Hint: We will provide up to two hints per challenge.
You can view them at the problem page (Submission site > Lab it > Problem name > Show)
Some hints (typically for the first five challnges of each lab) are free.
The others will cost one point for opening.
You can check if the hint is free or not by clicking the “Show” button.
Late policy: 50% of the original points (only within one week past the due date).
Write-ups¶
You must submit a write-up for each challenge to get the actual points.
Your write-up must be in plain text formatted by markdown syntax
Your write-up must contain
a simple description of how you solved the challenge, and
the actual exploit (i.e., code!).
Your write-up must be specific enough that we can run and validate your exploit ourselves.
You don’t need to submit write-ups for the tutorial challenges.
Here is an example write-up:
1) Write-up:
This binary stores its return addresses and frame pointers in a separate
stack; while we can overwrite those values on the regular stack, it
accomplishes nothing.
`main()` puts a pointer to `exit()` in its stack frame, which it jumps to
after `start()` finishes. We can overwrite this during `start()`'s buffer
overflow to instead point to `jump_to_here()`, which prints the flag.
Conveniently, due to the return-address protection and the fact that
`start()` doesn't have many meaningful local variables, we don't need
to be careful about the other values we clobber on the stack on the way
to `main()`'s local function pointer. The correct return addresses are
restored at the end of each function.
2) Exploit:
#!/usr/bin/env python3
from pwn import *
p = process('./target')
p.sendline(cyclic(52) + p32(0x8048948)) # (jump_to_here())
p.interactive()