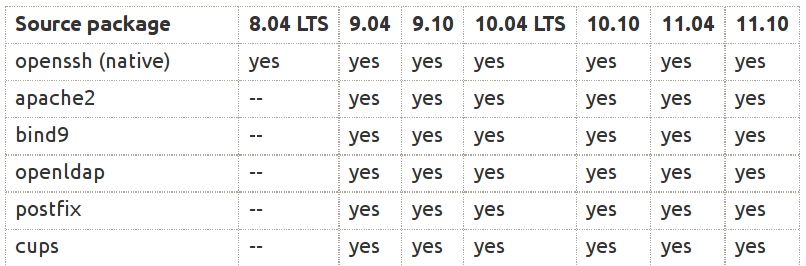
Configurations
Taesoo Kim
2014-08-25

$ getcap =ping
/usr/bin/ping = cap_net_raw+ep
CAP_NET_RAW
* use RAW and PACKET sockets;
* bind to any address for transparent proxying.
@/etc/apparmor.d/abstractions/bash
# user-specific bash files
@{HOMEDIRS} r,
@{HOME}/.bashrc r,
@{HOME}/.profile r,
@{HOME}/.bash_profile r,
@{HOME}/.bash_history rw,
# system-wide bash configuration
/etc/profile r,
/etc/profile.d/ r,
/etc/profile.d/* r,
... /usr/sbin/tcpdump {
capability net_raw,
capability setuid,
capability setgid,
# for -D
capability sys_module,
@{PROC}/bus/usb/ r,
@{PROC}/bus/usb/** r,
# for -z
/bin/gzip ixr,
/bin/bzip2 ixr,
...
}
push %ebp
mov %esp,%ebp
...
leave
ret push %ebp
mov %esp,%ebp
mov %gs:0x14,%eax ; load stack canary using gs
mov %eax,-0xc(%ebp) ; save it in the stack frame
xor %eax,%eax ; clear the register
mov -0xc(%ebp),%eax ; load canary
xor %gs:0x14,%eax ; compare against one in gs
je end
call __stack_chk_fail
leave
ret // &main = 0x400753
void main() {
if (setjmp(jump_point) == 0) {...}
}
// &jump_point
-[JB_BX] 0 0x6012c0: (nil)
![JB_BP] 1 0x6012c8: 0x939a81f2bc976cfb
-[JB_12] 2 0x6012d0: 0x400640
-[JB_13] 3 0x6012d8: 0x7fff3315a600
-[JB_14] 4 0x6012e0: (nil)
-[JB_15] 5 0x6012e8: (nil)
![JB_SP] 6 0x6012f0: 0x939a81f2bef76cfb
![JB_PC] 7 0x6012f8: 0x6c64e759e60f6cfb (-> around 0x400753) $ diff <(cat /proc/self/maps) <(cat /proc/self/maps)
...
00400000-0040c000 r-xp ... /usr/bin/cat
0060b000-0060c000 r--p ... /usr/bin/cat
0060c000-0060d000 rw-p ... /usr/bin/cat
-01a14000-01a35000 rw-p ... [heap]
+00f0a000-00f2b000 rw-p ... [heap]
-7f2fd4d52000-7f2fd4ef6000 r-xp ... /usr/lib/libc-2.19.so
+7f6caefd5000-7f6caf179000 r-xp ... /usr/lib/libc-2.19.so
-7fff8b878000-7fff8b89a000 rw-p ... [stack]
+7fff5786d000-7fff5788f000 rw-p ... [stack]
...
$ ./checksec.bash --dir /sbin | grep "PIE enabled"
Canary found PIE enabled /sbin/dhclient
Canary found PIE enabled /sbin/init
No canary found PIE enabled /sbin/initctl
Canary found PIE enabled /sbin/mkntfs
No canary found PIE enabled /sbin/mntctl
Canary found PIE enabled /sbin/mountall
No canary found PIE enabled /sbin/mount.fuse
Canary found PIE enabled /sbin/ntfsclone
Canary found PIE enabled /sbin/reboot
Canary found PIE enabled /sbin/runlevel char buf[0x100];
strcpy(buf, s); // strcpy(buf, s)
mov 0x8(%ebp),%eax ; load parameter `s` to eax
mov %eax,0x4(%esp) ; save parameter for strcpy
lea -0x108(%ebp),%eax ; count `buf` in eax
mov %eax,(%esp) ; save parameter for strcpy
call 8048320 <strcpy@plt> // strcpy(buf, s) -> __strcpy_chk(buf, s, buflen)
movl $0x100,0x8(%esp) ; save value 0x100 as parameter
mov 0x8(%ebp),%eax ; load parameter `s` to eax
mov %eax,0x4(%esp) ; save parameter for strcpy
lea -0x108(%ebp),%eax ; count `buf` in eax
mov %eax,(%esp) ; save parameter for strcpy
call 8048370 <__strcpy_chk@plt> $ ./checksec.bash --dir /sbin | head
RELRO FILE
Partial RELRO /sbin/a2p
Partial RELRO /sbin/a52dec
Partial RELRO /sbin/aafire
Full RELRO /sbin/dhclient
... $ dmesg | grep NX
[ 0.000000] NX (Execute Disable) protection: active
$ cat /proc/cpuinfo | grep nx
flags : ... tsc msr pae apic mtrr pge ... nx
$ ./checksec.bash --dir /sbin | head
NX FILE
NX enabled /sbin/a2p
NX enabled /sbin/a52dec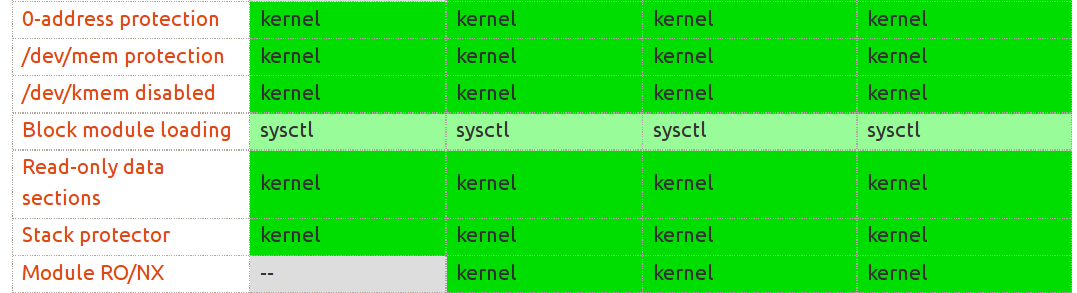
$ sysctl -a | grep mmap_min_addr
vm.mmap_min_addr = 65536 int devmem_is_allowed(unsigned long pagenr) {
if (pagenr <= 256)
return 1;
if (!page_is_ram(pagenr))
return 1;
return 0;
}